Enterprises have transformed how they use workplace and therefore IT for commercial buildings has changed. Legacy cybersecurity approaches no longer work. Join CEO Karl May dives into this shift and how how digital workplace infrastructure is tackling this issue.
VIEW PRESENTATION:


VIDEO TRANSCRIPT:
Good afternoon My name is Karl May. Founder and CEO of Join, Join is based in San Francisco California. We are revolutionizing the way that networks are deployed and our mission statement is listed up here on the screen is about connecting people to their work what I'm going to do today as I'm first going to tell you a little bit about what we as a company do what we as a company do. I'm going to talk primarily about how we address or but some of the risks are with regard to cyber risk not only Visa V what a lot of people can talk about here which is for building management systems but also for your tenants. Need to talk a little bit about how we address it how traditional strategies simply fail and how we address it. And then if there aren't any questions afterward I'll be happy to address them. So let me give you a little walkthrough on us. Join us founded about two and a half years ago really with the sponsorship of several large Fortune 500 companies that saw a fundamental shift in the way information technology is consumed.
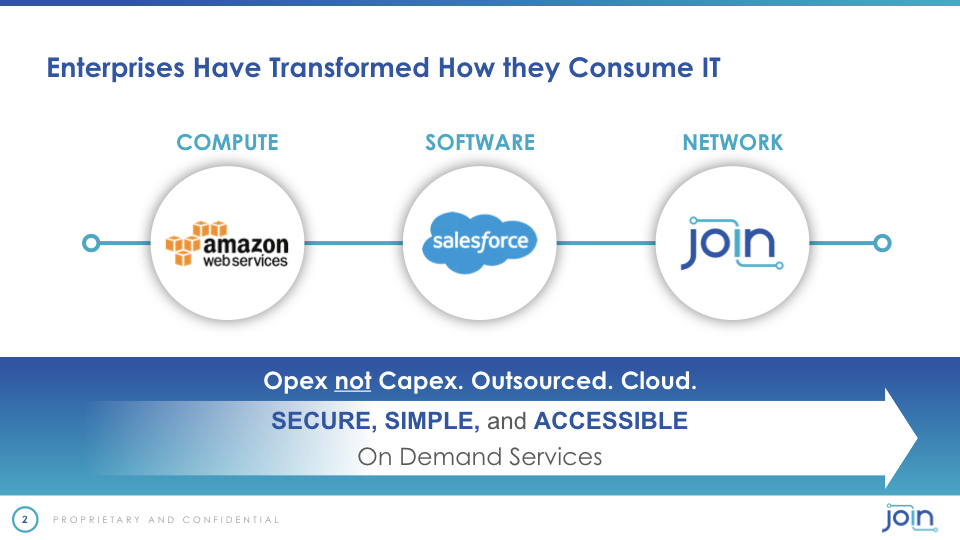
We all know that Amazon but Amazon has done the computing and frankly the storage of data. We know what Salesforce started 20 years ago and changing the way software is consumed by our. Applications are consumed. And what we're doing is the same thing really to the network.
The idea is that we can actually deploy a network or the edge of the cloud which is where everything resides nowadays in a in a in a neat in an apex in an in an OPIC centric not CapEx fashion that is managed and that is that lives in the cloud. And that's really what what we do
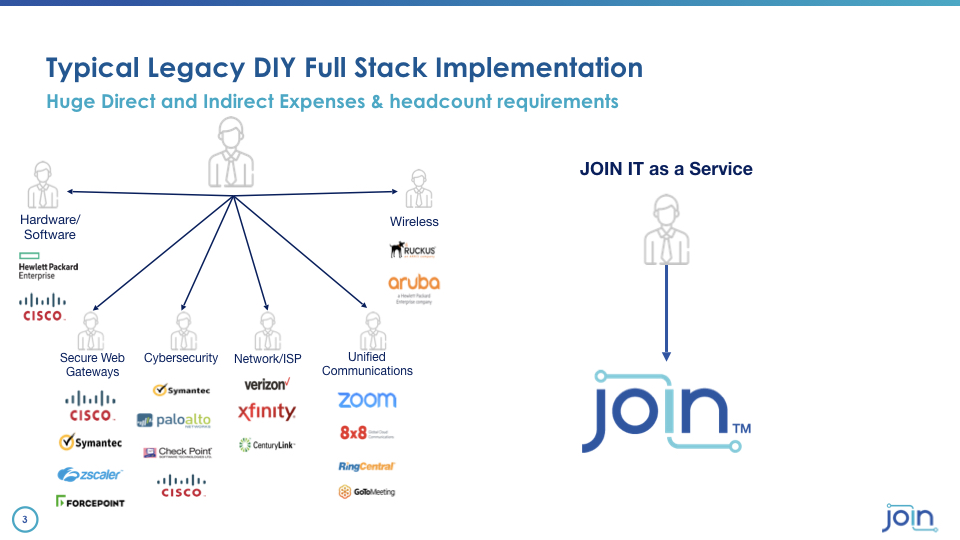
We focus primarily on delivering services over our own network. We are not we don't we don't interact with all the other carriers we've built our own and we deliver I.T. services over that network. Now if you look at a traditional way that companies deploy these tenants or frankly even building owners deploy networks in their buildings there is a hodgepodge of vendors they have to deal with their vendors for circuits their vendors for hardware they've got to put all these things together and make them work the magic that we bring to the table now that we provide all of this as an on demand service we build our own tech stack from the hardware frankly from the optics
On up to the software and we deliver that as an on demand service in partnership with the owners of commercial real estate assets. Now I want to shift to the main topic that I want to talk about here which is cyber security risk. And one of the big issues that we're seeing more and more and we read about more and more is the is the attacks or threats that come from third parties not just not insiders but from third parties attacking corporate networks. And those corporate networks also include by the way the networks that are operated by building owners to which they connect their building management systems their sensors and other sorts of I.T.
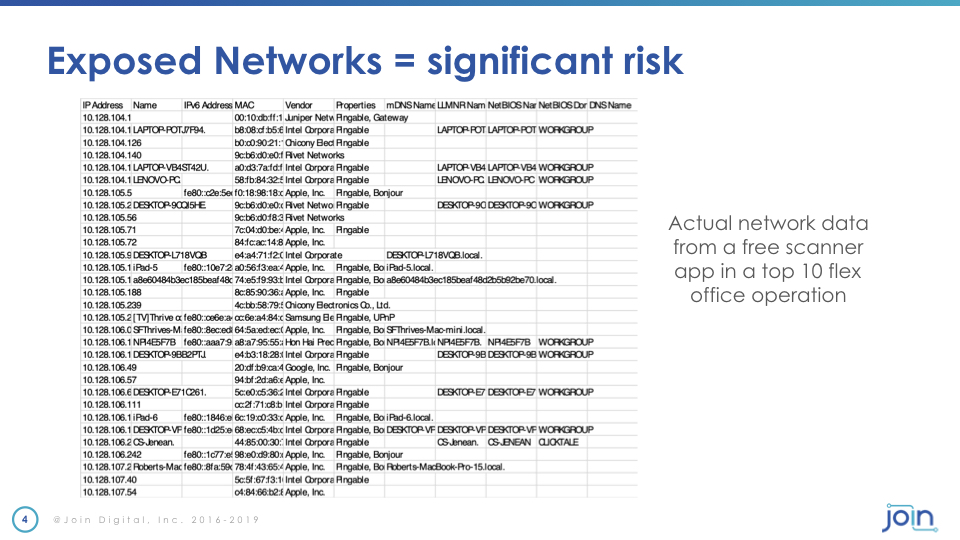
devices. This is a real live it's not live but it's a real output of a scan that we did in about 80 sites around the country. This is from one particular site. This is a real output of a Wi-Fi scan of one of the name of a name brand coworking provider probably known to many of you here. This is the level while everybody thinks I'm safe because I'm I'm using a VPN or UN or I'm encrypting my data or whatnot but they don't realize that I can actually see all their devices.
I can see your Android phone I can see you. Which Mac you have I can see your MAC address. I can get all this data into a malicious outsider. I can now install a botnet and automate or credit cron job to go stand this on a continuous basis to figure out whether vulnerabilities and the reality is is that we have in many ways been far too complacent about cybersecurity. I mean we can talk about passwords we can talk about VPN or other things but the reality reality is is that many companies are far too complacent.
If we weren't we would not be seeing the sorts of enormous breaches in companies like Equifax and target and so forth. Our view is very simple and that is that traditional ways of addressing cyber security are simply inadequate. The reality is as a conventional networking technologies are really designed to move on. I really designed to allow for discovery. I use some technical terms they're used for discovery of what other resources are sitting on a network. And the problem is is this opens up your neighbor network. So if you're a tenant in the building the the Wi-Fi network next door could very easily become or your network could very easily become a target of your neighbors.
And so our approach has been very very simple. We work together with the owner. We secure the entire building and all of the network connectivity into that building to our private cloud our cloud is where we have all of our own connections to the public internet to public clouds to data centers to SaaS providers. We then put in place our own cybersecurity elements at that border which is where we deflect and or or detect and then deflect threats.
It's where we protect against intrusions and so forth. And then we provide the entire solution into the building not only for the tenant but also for the building management system. So if you look at the rise of cameras based I.T. devices we provide all of those elements their own private network that is secured by us the premise on which we do this is something called zero trust it's actually a new concept. The concept has come about in the last couple of years. It's the notion that in a world where we have mobile workers we have our work that which we work on is sitting in the cloud. We have to have traditional perimeters anymore. And so therefore we need not to trust who you are because of where you are in a building or in an office but because of who you are. And so zero trust simply says that we don't trust anybody or anything.
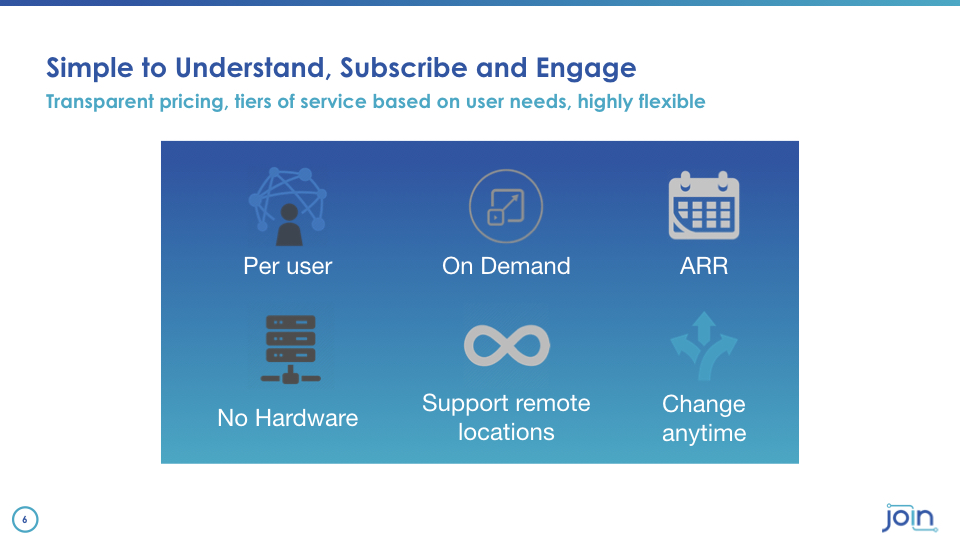
We validate devices and we develop validate users independent of where they are and only those users are the ones that get access. To the network resources or the services that we deliver. And that's really the fundamental premise of what Join has built on zero trust. To summarize let me talk a little bit about our business model and then I think if there are any questions I'm happy to know some. We don't see it as most. Most providers today deliver services that are based on old models such as bandwidth and and selling bits and bandwidth and so forth. Our model is very simple. We bring terabytes of bandwidth into a site into a building we charge per user per service type. There is no hardware no hardware to assemble.
No it's not an IKEA model where you've got to go get 8 or 10 boxes to work together. We take care of all of that. It's an on demand service. You pay for a subscription you pay for it as your organization grows or shrinks you pay more or you pay less. And we believe that fundamentally applying SaaS business model principles to the network as well as all of our cybersecurity is what is going to change the way I.T. is consumed in the offices both of today and of the future.
And I thank you very much for your time.



